Trezor.io/start – Unlock True Crypto Ownership with Secure Setup
Your Crypto Journey Begins with Security
When stepping into the world of digital assets, the first and most important move is securing your holdings. If you’ve invested in a Trezor hardware wallet, your first destination should be Trezor.io/start. This official setup page provides all the tools and instructions you need to configure your wallet safely and efficiently, protecting your assets from hackers, phishing attacks, and loss.
Starting at Trezor.io/start ensures you avoid counterfeit applications or malicious downloads—your strongest defense starts at the source.
What Is the Trezor Hardware Wallet?
Offline Protection for Your Digital Wealth
The Trezor hardware wallet is a physical device designed to store your cryptocurrency's private keys offline. Unlike hot wallets that connect to the internet, Trezor remains disconnected until needed, drastically reducing exposure to cyber threats.
Whether you hold Bitcoin, Ethereum, or dozens of other cryptocurrencies, the Trezor hardware wallet provides:
- Cold storage for top-level security
- PIN and passphrase protection
- Compatibility with multiple blockchain networks
To activate these features, go to Trezor.io/start, the only reliable place to begin setup.
Getting Started at Trezor.io/start
Your Complete Setup Path
To prepare your wallet for safe use:
-
Connect Your Trezor Device
Plug in your Trezor Model One or Model T. -
Navigate to Trezor.io/start
This official page guides you through every required step. -
Install Trezor Suite
Download the secure app for desktop crypto management. -
Set Up a New Wallet or Recover One
Follow instructions to create a seed phrase or restore one. -
Configure Security Settings
Assign a PIN and enable advanced features like passphrase protection. -
Begin Using Your Wallet
You're now ready to send, receive, stake, and manage your assets with confidence.
Everything at Trezor.io/start is designed with user-friendliness and security in mind.
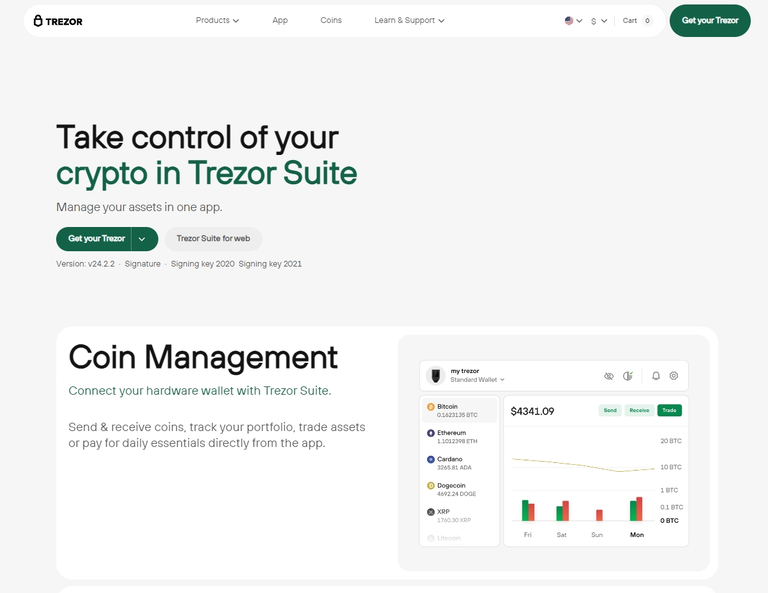
Trezor Suite: Manage Crypto Securely and Easily
One Dashboard for Everything You Need
Trezor Suite is the official desktop application that works seamlessly with your Trezor device. After setup through Trezor.io/start, this software becomes your command center for everything from transactions to staking.
Key features include:
- Multi-currency support and real-time portfolio tracking
- Built-in exchanges for asset swaps
- Integration with hardware wallet for added security
- Access to Trezor staking options
- Regular updates and privacy tools like Tor support
Trezor Suite isn’t just convenient—it’s built to protect your digital assets at every touchpoint.
Trezor Bridge: Seamless Communication for Browser Access
Invisible but Powerful Integration
If you’re using a web browser to interact with your wallet or dApps, Trezor Bridge plays a vital role. This background service allows secure communication between your Trezor hardware and your computer’s browser.
After visiting Trezor.io/start, you’ll be prompted to install Trezor Bridge if it’s required for your system. Once installed, it runs silently, ensuring:
- Safe browser-wallet interactions
- Stable performance during web-based transactions
- Elimination of risky browser extensions
Trezor Bridge ensures security without sacrificing usability.
Trezor Login: Protect Your Web3 Identity
Passwordless Authentication for the Future
As decentralized applications grow in popularity, login security becomes more crucial than ever. With Trezor login, users can authenticate across Web3 platforms using cryptographic signatures instead of passwords.
This login method offers:
- Phishing-resistant authentication
- Easy access to dApps and exchanges
- No need to store or remember passwords
Available after setup at Trezor.io/start, this feature enables secure access to services with a single device click—your private keys stay offline the entire time.
Trezor Staking: Grow Your Assets Safely
Earn Rewards Without Giving Up Control
Trezor staking is the process of locking certain cryptocurrencies to earn passive rewards—all without giving up custody. Through third-party integrations within Trezor Suite, users can delegate coins to network validators securely.
Supported staking options include:
- Cardano (ADA)
- Tezos (XTZ)
- Polkadot (DOT)
Each staking action is verified on your Trezor hardware wallet, ensuring full control of your funds while you earn crypto rewards. All of this is possible once setup is complete via Trezor.io/start.
Ongoing Security Tips After Setup
Best Practices to Keep Your Assets Safe
After initializing your wallet at Trezor.io/start, follow these essential practices:
- Back up your recovery seed and store it offline
- Never share your seed with anyone
- Use a unique PIN and enable a passphrase
- Update Trezor Suite and firmware regularly
- Avoid downloading apps from unofficial sources
These simple steps help extend the core security you gain from Trezor.
Final Thoughts: Begin with Trezor.io/start for Trusted Crypto Security
The road to safe and independent cryptocurrency ownership begins with one secure action—visiting Trezor.io/start. This verified page ensures your Trezor hardware wallet is set up using official tools like Trezor Suite and Trezor Bridge, and prepares you to use advanced features like Trezor login and Trezor staking.
Don’t compromise your crypto holdings. Start with the right tools, the right way, and from the right place: Trezor.io/start.